Types of Security in Dynamics CRM
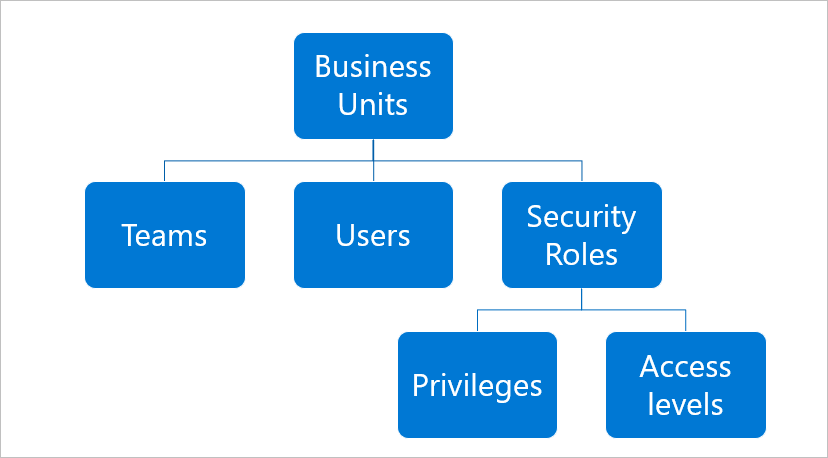
MS Dynamics CRM provides three types of security:
- Role-based security
- Record based security
- Field level security
Role-based security: It provides a specific set of privileges to a user in Dynamics 365
For example: If we want all users with the security role of sales manager to have read, write, and delete access to all Lead records while users with the security role of salesperson should have only read access to the Leads they own, role-based security settings help accomplish this.
Record-based security: It allows or restricts access to specific records in the CRM.
For example: If we want to restrict a set of users from accessing Case records, record-based security helps accomplish this.
Field level security: It allows or restricts access to specific fields on an entity in Dynamics CRM.
For example: If we want only a set of users to see a specific field (Annual Revenue, for instance) on the Lead entity, field-based security can hide or display that field, based on users.
A new security role can be created in different ways.
To create a security role from scratch
To modify a CRM default role
To copy an existing role and modify its privileges.
Ideal way:
The ideal way to create a new security role is to copy an existing role and then modify its privileges. Dynamics CRM contains 580 predefined privileges, so it is difficult to create a new security role from scratch.
To View or Set Privileges to a Security Role:
1. Navigate to Settings-> Security->Security Roles
It will list all the security roles available in CRM. Open the security role that you want to modify. You can set privileges to that security role based on the various access levels provided.
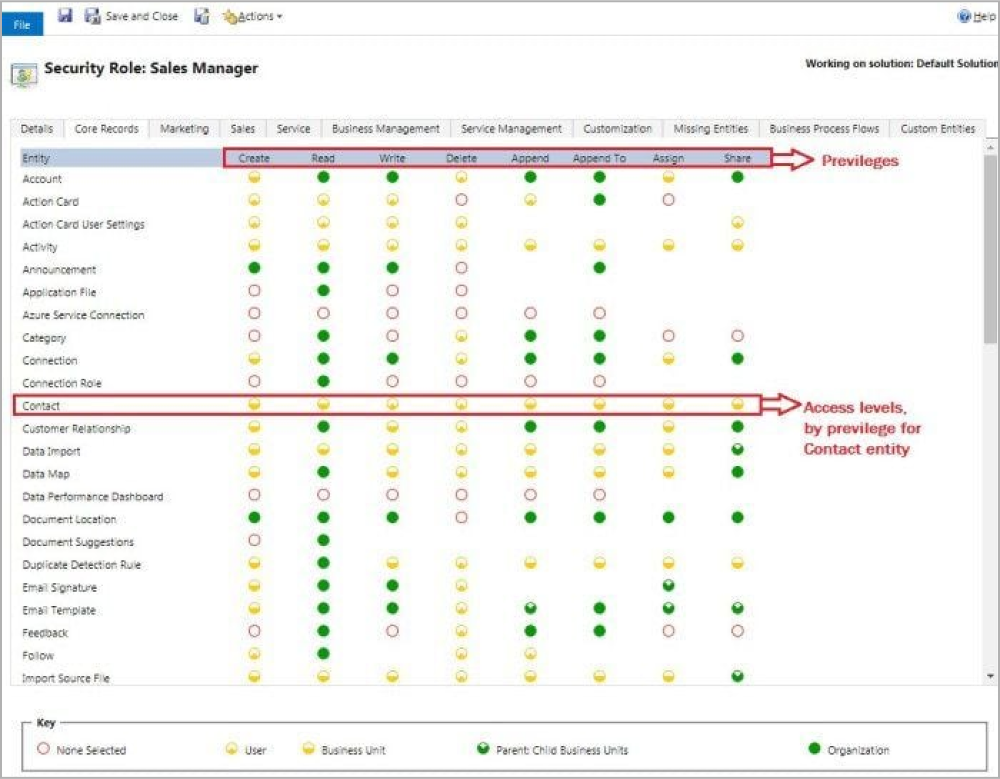
Levels of Access:
None: No Privileges given.
User (Basic): The privilege will be given to the records owned by the user and the team to which the user belongs.
Business Unit (Local): Privileges to records owned by the business unit to which the user belongs.
Parent (Deep): Privileges to the records owned by the parent business unit to which the user belongs and the child business units associated with that business unit.
Organization (Global): Privileges for all records in the organization regardless of who owns it.
Security Role Design:
When enterprise BU structure is confirmed and approved by the business:
- We can initialize the conversation and provide the questionnaire to the business team.
In the questionnaire spreadsheet, there would be a set of breakdown questions to the business for the privileges design and dicussion.
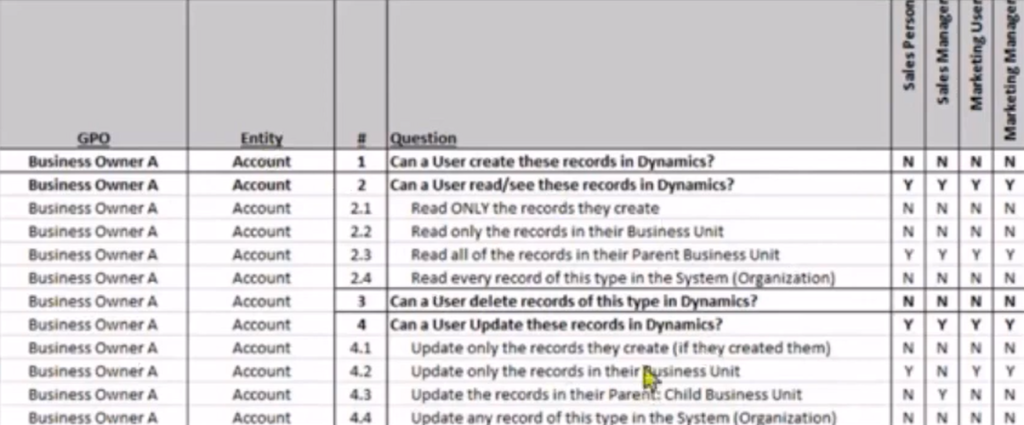
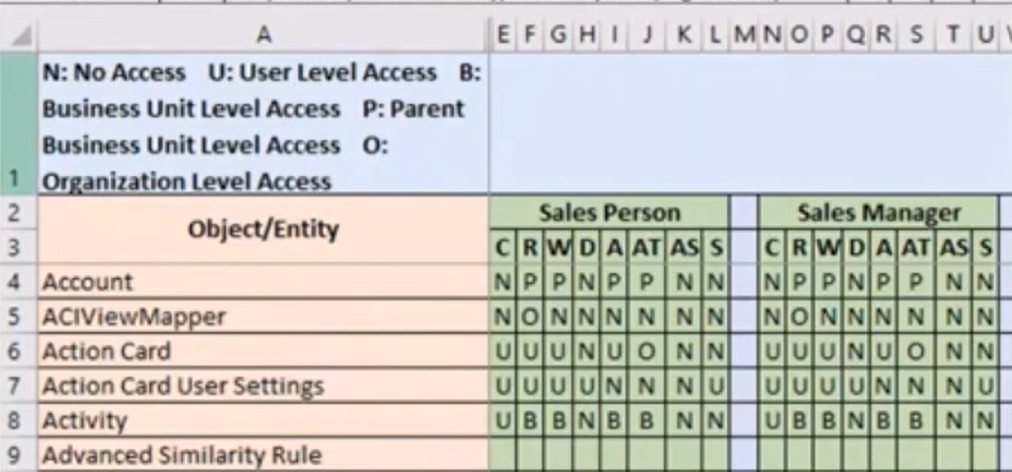
2. Mapping to the security matrix design document.
(1) By using the default object and entity in D365
(2) Customize the security role based on business feedback
(3) Setup the access for each privilege.
3. Continuously updating during SIT/UAT stage
(1) Bugs would be raised during the testing stage
(2) Business/Security teams meetings and feedbacks